:star2: Highlights
GCC Static Analyzer support
We are happy to announce that CodeChecker added native support for the [GCC Static Analyzer](https://gcc.gnu.org/wiki/StaticAnalyzer)! This analyzer checks code in the C family of languages, but its latest release at the time of writing is still best used only on C code. Despite it being a bit immature for C++, we did some internal surveys where the GCC Static Analyzer seemed to be promising.
We expect this analyzer to be slower than clang-tidy, but faster than the Clang Static Analyzer. You can enable it by adding `--analyzers gcc` to your `CodeChecker check` or `CodeChecker analyze` commands. For further configuration, check out the [GCC Static Analyzer configuration page](https://github.com/Ericsson/codechecker/blob/master/docs/analyzer/checker_and_analyzer_configuration.md#gcc-static-analyzer).
GNU GCC 13.0.0. (the minimum version we support) can be tricky to obtain and to make CodeChecker use it, as CodeChecker looks for the `g++` binary, not `g++-13`. As a workaround, you can set the environmental variable `CC_ANALYZER_BIN` which will make CodeChecker use the given analyzer path (e.g. `CC_ANALYZER_BIN="gcc:/usr/bin/g++-13"`). You can use `CodeChecker analyzers` to check whether you have the correct binary configured.
You can enable gcc checkers by explicitly mentioning them at the analyze command e.g.
CodeChecker analyze -e gcc
gcc checkers are only added to the exterme profile. After evaluation, some checkers may be added to other profiles too.
Under the same breath, we added partial support for the [SARIF](https://sarifweb.azurewebsites.net/) file format (as opposed to using plists) to `report-converter`, with greater support planned for future releases.
Review status config file
In previous CodeChecker versions, you could set the review status of a report using two methods: using [in-source comments](https://github.com/Ericsson/codechecker/blob/master/docs/analyzer/user_guide.md#setting-with-source-code-comments), or setting a [review status rule](https://github.com/Ericsson/codechecker/blob/master/web/server/vue-cli/src/assets/userguide/userguide.md#review-status) in the GUI. The former sets the specific report's review status, the latter sets all matching reports' review status.
This release introduces a third way, a review status config file! One of the motivations behind this is that we wanted to have a way to set review statuses on reports in specific directories (which was not possible on the GUI). CodeChecker uses a YAML config file that can be set during analysis:
yaml
review_status.yaml
- filepath_filter: /path/to/project/test/*
checker_filter: core.DivideZero
message: Division by zero in test files is automatically intentional.
review_status: intentional
- filepath_filter: /path/to/project/important/module/*
message: All reports in this module should be investigated.
review_status: confirmed
- filepath_filter: "*/project/test/*"
message: If a filter starts with asterix, then it should be quoted due to YAML format.
review_status: suppress
- report_hash_filter: b85851b34789e35c6acfa1a4aaf65382
message: This report is false positive.
review_status: false_positive
This is how you can use this config file for an analysis:
bash
CodeChecker analyze compile_commands.json --review-status-config review_status.yaml -o reports
The config file allows for a great variety of ways to match a report and set its review status. For further details see [this documentation](https://github.com/Ericsson/codechecker/blob/master/docs/analyzer/user_guide.md#setting-with-config-file).
Enable/disable status of checkers
In previous CodeChecker versions, when you ran an analysis, we assigned three states to every checker: it's either **enabled**, **disabled**, or **neither** (unknown). We kept the third state around to give some leeway for the analyzers to decide which checkers to enable or disable, usually to manage their checker dependencies. We now see that this behavior can be (and usually is) confusing, party because it's hard to tell which checkers were actually enabled.
In this release the *unknown* status has been eliminated, and we deal with dependencies using other means. Moving on, CodeChecker will enable only those checkers that are either present in the *default* profile (see `CodeChecker checkers --profile default`) or enabled using the `--enable` argument.
Major fixes to run/tag comparisons (diff)
Following a thorough survey, we identified numerous areas to improve on our run/tag comparisons. We landed several patches to improve the results of diffs both on the CLI and the web GUI (which should be almost always identical). Despite that this feature has the appearance of a simple set operation, diff is a powerful tool that can express a lot of properties on the state of your codebase, and has a few intricacies. For this reason, we also greatly improved [our docs](https://github.com/Szelethus/codechecker/blob/diff_docs_rewrite/docs/web/diff.md) around it.
Web GUI improvements
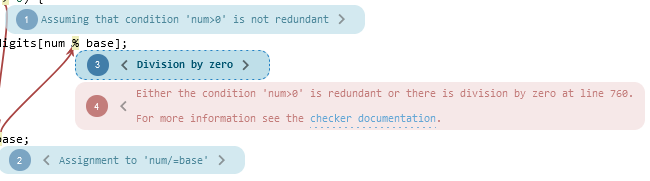
We landed several patches to improve the readability and usability of the GUI, with more improvements to come in later releases! The currently selected event's visual highlight pops a little more now in the report view, and we no longer show unused columns in the run view.
In this image, you can see how much the selected event "pops" after this release, and also, how other events' opacity was a lowered a bit, which allows arrows to be seen through them.
Report limit for storing to the server
Especially in the case of clang-tidy, we have observed some unreasonable number of reports by certain checkers. In some instances, we saw hundreds of thousands (!) of reports reported by some individual checkers, and its more than unlikely that anyone will inspect these reports individually (you probably got the message about using parantheses around macros after the first 15 000 reports).
We found that these checkers were usually enabled by mistake, and put unnecessary strain both on the storage of results to the server, and on the database once stored. Moving forward, CodeChecker servers will reject stores of runs that have more than 500 000 reports. This limit is a default value that you can change or even set to unlimited. Our intent is not to discourage legitemately huge stores, only those that are whose size is likely this large by mistake.
When creating a new product called `My product` at [endpoint](https://github.com/Ericsson/codechecker/blob/869a8ad938925919eca2008a829ef44737649b7e/docs/usage.md#step-6-store-analysis-results-in-a-codechecker-db-and-visualize-results) `myproduct`, you can set the report limit from the CLI with the following invocation:
bash
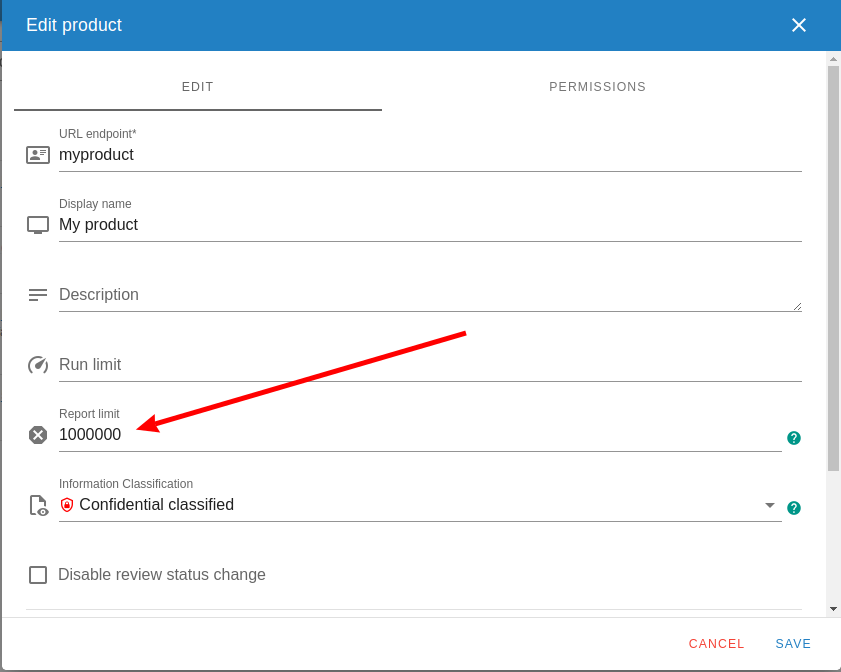
CodeChecker cmd products add -n "My product" --report-limit 1000000 myproduct
For an already existing product, you can change the limit by clicking the pencil at the products page:

:exclamation: Backward incompatible changes
Clang warnings must be referred to as `clang-diagnostic-<warning-name>` (instead of `W<warning-name>`)
After analysis, reports from clang compiler warnings (well before this release) were attributed to `clang-diagnostic-<warning-name>` instead of `-W<warning-name>` that is usually given to the compiler to enable `<warning-name>`. We did this so that warnings from different compilers could be differentiated. However, you could only enable `<warning-name>` as a checker by referencing it as `W<warning-name>`. In this release, we fixed this inconsistency.
Moving forward, you can enable a clang warning with the following syntax:
CodeChecker analyzer -e clang-diagnostic-deprecated-copy
instead of
CodeChecker analyze -e Wdeprecated-copy
which is no longer supported. You can list all clang-diagnostics with the `CodeChecker checkers` command.
`--all` and `--details` were deprecated for `CodeChecker analyzers`
With the introduction of the GCC Static Analyzer, we think that the `--all` flag was more confusing than useful -- its a reasonable assumption that any system will have a version of GCC available. The default behaviour prior to this release was to only list analyzers that were _available_ for analysis: the binary was found, met the version criteria, and was functional. The `--all` flag listed all _supported_ analyzers, even if they were not _available_. We changed the default behaviour to always list all _supported_ checkers, and `--all` is ignored. We emit helpful warnings for analyzers that CodeChecker supports, but can't analyze with.
`--details` could be used to print additional version information of the binary, but we didn't feel like it provided any value above what the non-detailed query gave, and it was impossible to pretty print. After this release, this flag will also be ignored.
:bug: Analyzer improvements
* [fix] Recognize -pthread for gcc compile commands https://github.com/Ericsson/codechecker/pull/3969
* [bugfix] Allow the disabling of statisticsbased checkers https://github.com/Ericsson/codechecker/pull/3972
* [bugfix] Include platform to `ldlogger.so` path https://github.com/Ericsson/codechecker/pull/3976
* [analyzer] Ignore another unknown gcc options https://github.com/Ericsson/codechecker/pull/4028
* [report-converter] Support sarif format and Gcc analyzer https://github.com/Ericsson/codechecker/pull/4011
* **Gcc analyzer native support https://github.com/Ericsson/codechecker/pull/4030**
* [clang-tidy] Fix Clang tidy checker option output https://github.com/Ericsson/codechecker/pull/4050
* [analyzer] Add support the CC_ANALYZER_BIN env var https://github.com/Ericsson/codechecker/pull/4057
:computer: CLI/Server improvements
* Eliminate "unknown" checker state https://github.com/Ericsson/codechecker/pull/3949
* **[bugfix] Don't trigger analyzer without enabled checkers https://github.com/Ericsson/codechecker/pull/3970**
* [fix] Refine when a report is regarded as outstanding for tags https://github.com/Ericsson/codechecker/pull/3995
* [cmd] Fix FP annotations in the case of local-remote diffs https://github.com/Ericsson/codechecker/pull/3956
* [diff] Fix a CLI remote-remote bug where we checked the detection status https://github.com/Ericsson/codechecker/pull/3996
* [cmd][diff] Ignore detection status for tags https://github.com/Ericsson/codechecker/pull/4013
* [gui] Update run filter when setting the filter options https://github.com/Ericsson/codechecker/pull/3963
* replace os.uname() with platform.uname() for Windows support https://github.com/Ericsson/codechecker/pull/4012
* [feat] Introduce review status config file https://github.com/Ericsson/codechecker/pull/4054
* [fix][clang-tidy] Fix env var replace for extra args https://github.com/Ericsson/codechecker/pull/4033
* [enhancement] --cppcheckargs flag was missing https://github.com/Ericsson/codechecker/pull/3978
* feat(store): Explicitly time the client out if the connection hung https://github.com/Ericsson/codechecker/pull/4039
* **[server] Rate limit based on report count https://github.com/Ericsson/codechecker/pull/3843**
* [analyzers] Deprecate --all and --details for analyzers https://github.com/Ericsson/codechecker/pull/4056
* Parse file speed up https://github.com/Ericsson/codechecker/pull/4000
:deciduous_tree: Environment
* [req] Upgrade PyYAML to 6.0.1 https://github.com/Ericsson/codechecker/pull/3961
* [test] Fix package test https://github.com/Ericsson/codechecker/pull/3965
* [check actions] setting GITHUB_TOKEN permissions to read https://github.com/Ericsson/codechecker/pull/3983
* Create SECURITY.md https://github.com/Ericsson/codechecker/pull/3990
* [db] Eliminating duplicate key constraint violations https://github.com/Ericsson/codechecker/pull/3712
* Bump gitpython from 3.1.30 to 3.1.32 in /web https://github.com/Ericsson/codechecker/pull/3987
* Bump gitpython from 3.1.30 to 3.1.32 in /web/requirements_py/dev https://github.com/Ericsson/codechecker/pull/3985
* Bump cryptography from 3.3.2 to 41.0.3 in /web/requirements_py/dev https://github.com/Ericsson/codechecker/pull/3986
* Bump minimist from 1.2.5 to 1.2.8 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3993
* Bump word-wrap from 1.2.3 to 1.2.5 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3988
* Bump webpack from 5.66.0 to 5.76.0 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3991
* Bump json5 from 1.0.1 to 1.0.2 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3992
* Bump qs from 6.5.2 to 6.5.3 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3998
* Bump loader-utils from 1.2.3 to 1.4.2 in /web/server/vue-cli https://github.com/Ericsson/codechecker/pull/3999
* Bump gitpython from 3.1.32 to 3.1.34 in /web/requirements_py/dev https://github.com/Ericsson/codechecker/pull/4005
* Bump gitpython from 3.1.32 to 3.1.34 in /web https://github.com/Ericsson/codechecker/pull/4004
* Bump cryptography from 41.0.3 to 41.0.4 in /web/requirements_py/dev https://github.com/Ericsson/codechecker/pull/4015
* Bump gitpython from 3.1.34 to 3.1.35 in /web https://github.com/Ericsson/codechecker/pull/4016
* Bump gitpython from 3.1.34 to 3.1.35 in /web/requirements_py/dev https://github.com/Ericsson/codechecker/pull/4017
:book: Documentation updates
* Add more checks from clang-tidy https://github.com/Ericsson/codechecker/pull/3959
* [config] Add some checkers to "default" profile https://github.com/Ericsson/codechecker/pull/3971
* Document new clang-tidy checkers https://github.com/Ericsson/codechecker/pull/4024
* chore(config): Add labels for new checks of Clang SA & Tidy https://github.com/Ericsson/codechecker/pull/4051
* fix typo: 'hte' to 'the' https://github.com/Ericsson/codechecker/pull/3960
:hammer: Other
* [version] Bump up to version 6.23.0 https://github.com/Ericsson/codechecker/pull/3893
* [logger] + add missing header fcntl.h https://github.com/Ericsson/codechecker/pull/3958
* **[GUI] Change the selected bubble's brightness https://github.com/Ericsson/codechecker/pull/3981**
* [test] Add several more cmdline tests for tag diffs https://github.com/Ericsson/codechecker/pull/3979
* [bugfix] Make None assignments to be initializations, not overwrites https://github.com/Ericsson/codechecker/pull/4001
* [GUI] Jump directly to documentation url without error modal https://github.com/Ericsson/codechecker/pull/3974
* **[GUI] Unnecessary reports columns https://github.com/Ericsson/codechecker/pull/4014**
* [gui] Retain filter configuration between reports and statistics views https://github.com/Ericsson/codechecker/pull/4058
* [fix] Fix commentCount related error in gui https://github.com/Ericsson/codechecker/pull/4034
* Making an analyze and parse testcase checker set independent https://github.com/Ericsson/codechecker/pull/4045
* Fix typo in log https://github.com/Ericsson/codechecker/pull/4023
**Full Changelog**: https://github.com/Ericsson/codechecker/compare/v6.22.2...v6.23.0-rc1